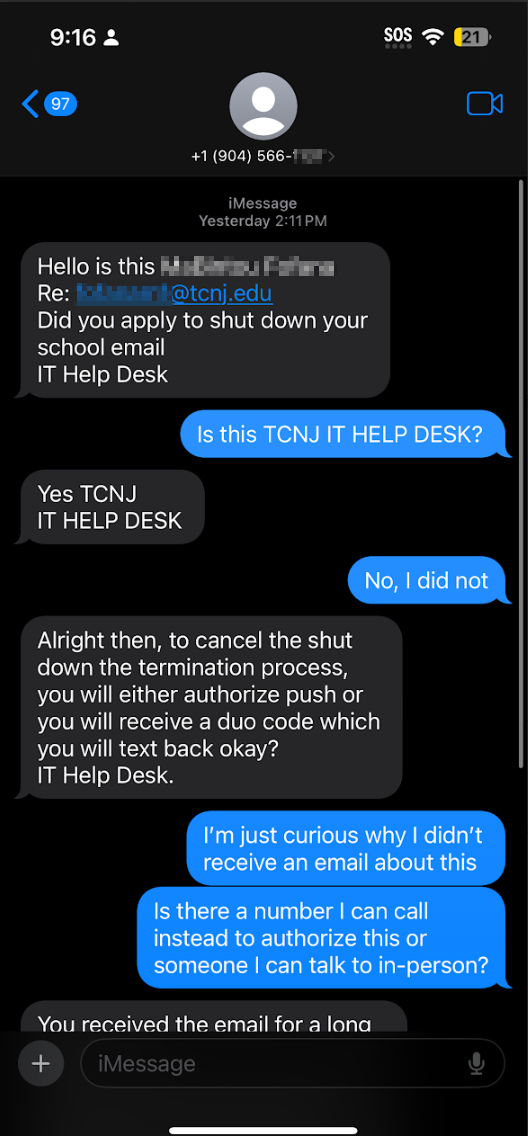
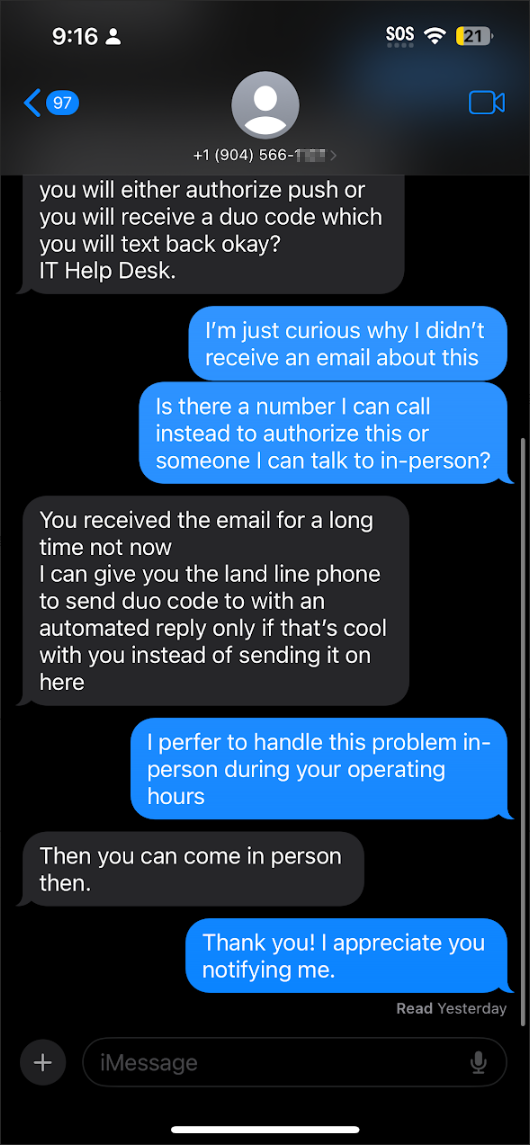
We have received reports that TCNJ users are receiving text messages claiming to be from the help desk about a request that the user close their school email address. The TCNJ help desk will not contact you about matters such as this via text message. Note in the screenshots below, the phone number does not begin with a NJ area code. If you receive any suspicious text messages, do not interact with the sender, do not click on any links provided and do not provide Duo codes or approve Duo pushes you did not initiate. Receiving text messages such as these does not necessarily mean they have your password, but if they anticipate that they can generate a Duo push to you, it may mean they do, in fact, know your password. Change your password immediately if you receive a text such as the one below. Please send any suspicious messages to us at phish@tcnj.edu. Thank you.
Author Archives: minsterg
[PHISH] July 2025 Salary Settlement_Approval Ref:-glY0Q4bUaNvfwrKclfGjyhoCYiubUB
We have received reports of a phishing email using a QR code to attempt to get users to follow a link to a fake Microsoft login page that will harvest user’s credentials. The email imitates TCNJ but does not come from a TCNJ email account. Scanning the QR code will lead to a fake captcha… Continue Reading
[PHISH] Review Completed: Tcnj management Settlement Agreement i
A phishing email utilizing an attachment with a QR code in it has been reported. The subject tries to engage the curiosity of the reader and prompt them to scan a QR code which leads to a malicious domain. This page will prompt the user to enter their credentials to view a document with the… Continue Reading
[PHISH] Salary Increment Letter – Effective June
We have received reports of a QR code phishing scheme claiming to contain details of a pay increase. Screenshots are below. The email utilizes an attachment that contains a QR code and prompts the user to scan it to view details. The link takes the user to a false Microsoft login page which prompts for… Continue Reading
[PHISH] Amended The College Of New Jersey Handbook Updated Policy
We received reports of a phishing email that claimed to contain an updated handbook for TCNJ. The email address of the sender is not a TCNJ address, which is a clear indicator that this is not legitimate. The attached PDF document contains a QR code that leads to a fake Microsoft login page; the URL… Continue Reading
[PHISH] Immediate Action Require: MFA System Upgrade
We received reports of an email utilizing a QR code attachment imitating TCNJ and warning of account lockout. Note the email did not come from a tcnj.edu email address and the entire email was an attachment. The QR code (if scanned) does not lead to a tcnj.edu website. Do not reply to the sender nor… Continue Reading
[PHISH] [TCNJ: Information Security Advisory] 2FA Authentication!
A number of users received a QR code phishing email this morning impersonating TCNJ. Note that the email originated from a Gmail account and not a TCNJ email address. The entire email body was an image rather than text, which attackers use to bypass filters. Do not scan the QR code. The landing page for… Continue Reading
[PHISH] Text Message Phish about Shutting Down Email
We’ve received some reports regarding another text message attack impersonating our help desk. Be aware our TCNJ Help Desk will not contact you via text message. You should also note that the area code of the phone number is outside the NJ area. Another point is that the attacker uses a sense of urgency in… Continue Reading
[PHISH] Chris Hann shared “HannWriting Inc.2025-03-18 14.07.29.pdf” with you
We are receiving reports of a phishing email utilizing Dropbox as a conduit to attempt to get users to download a malicious PDF. See example email below. Attackers often will use 3rd party services such as Dropbox to host malicious files and bypass spam filters. Be cautious of any file sharing links that you are… Continue Reading
[PHISH] Q1 Employee Handbook|Policy Reviews-88638-ZHDN-NHHD-UPQN
We have received reports about an attacker impersonating our HR department. See example email below. Note that the sender email address is not a tcnj.edu address. Hovering over the link also shows an unusual URL destination. The email also uses a TCNJ logo and enticing wording to attempt to lure people into clicking the link. … Continue Reading